
8 SBOM Best Practices for Medical Device Manufacturers
Ransomware attacks frequently target medical institutions, taking offline equipment connected to the internet, such as phones, email and electronic health records, until the victimized organization pays up. Last year, at least 299 hospitals suffered such attacks, according to the Institute for Security and Technology. One example among many: on January 31 hackers hit Chicago’s biggest children’s hospital, forcing it to significantly curtail services.
Amidst concern that hackers may grow more brazen and focus attention on compromising medical devices not just hospital systems, the Food and Drug Administration (FDA) now requires that device manufacturers create a Software Bill of Materials (SBOM) to improve transparency, traceability and cybersecurity. An SBOM is essentially a list of all open source and third-party software components, libraries and dependencies present in a medical device’s codebase.
They are intended to empower organizations to better manage and secure their applications. By providing a clear and detailed inventory of the software's building blocks, an SBOM offers visibility into potential vulnerabilities, aids in risk management, and is crucial for regulatory compliance and ensuring patient safety.
The SBOM mandate is part of the PATCH Act, which empowers the FDA to enforce stricter cybersecurity measures for medical devices as of October 1, 2023. While it should help safeguard the healthcare industry, it represents a substantial burden on device manufacturers as creating an SBOM is time-consuming and complex. The process is particularly onerous for large software applications with many dependencies.
Essential SBOM Best Practices
The concern that critical medical device software may not be properly secured or adequately protected from cybersecurity bad actors is warranted – a sizable number of medical devices run on outdated or unsupported operating systems, including Linux and other open-source software. That’s where a comprehensive and accurate SBOM can help – by making it faster and easier for organizations to identify new vulnerabilities and implement necessary fixes.
To streamline the SBOM creation process, we’ve outlined 8 impactful best practices manufacturers should follow.
1. Implement a Robust Secure Product Development Framework
The FDA strongly encourages manufacturers to create and follow robust security processes to identify and mitigate security vulnerabilities. A Secure Product Development Framework (SPDF) is a set of processes – encompassing all aspects of a product's lifecycle, including design, development, release, support and decommission – that help you identify and reduce the number and severity of vulnerabilities within a product.
ICS’ normative approach to cybersecurity is to define a SPDF derived from SW96, TIR 57, and IEC 81001 5-1, and the FDA guidance from October 2023. The graphic below offers a high-level outline of our SPDF, diagrammed in parallel to the Design Control process shown.
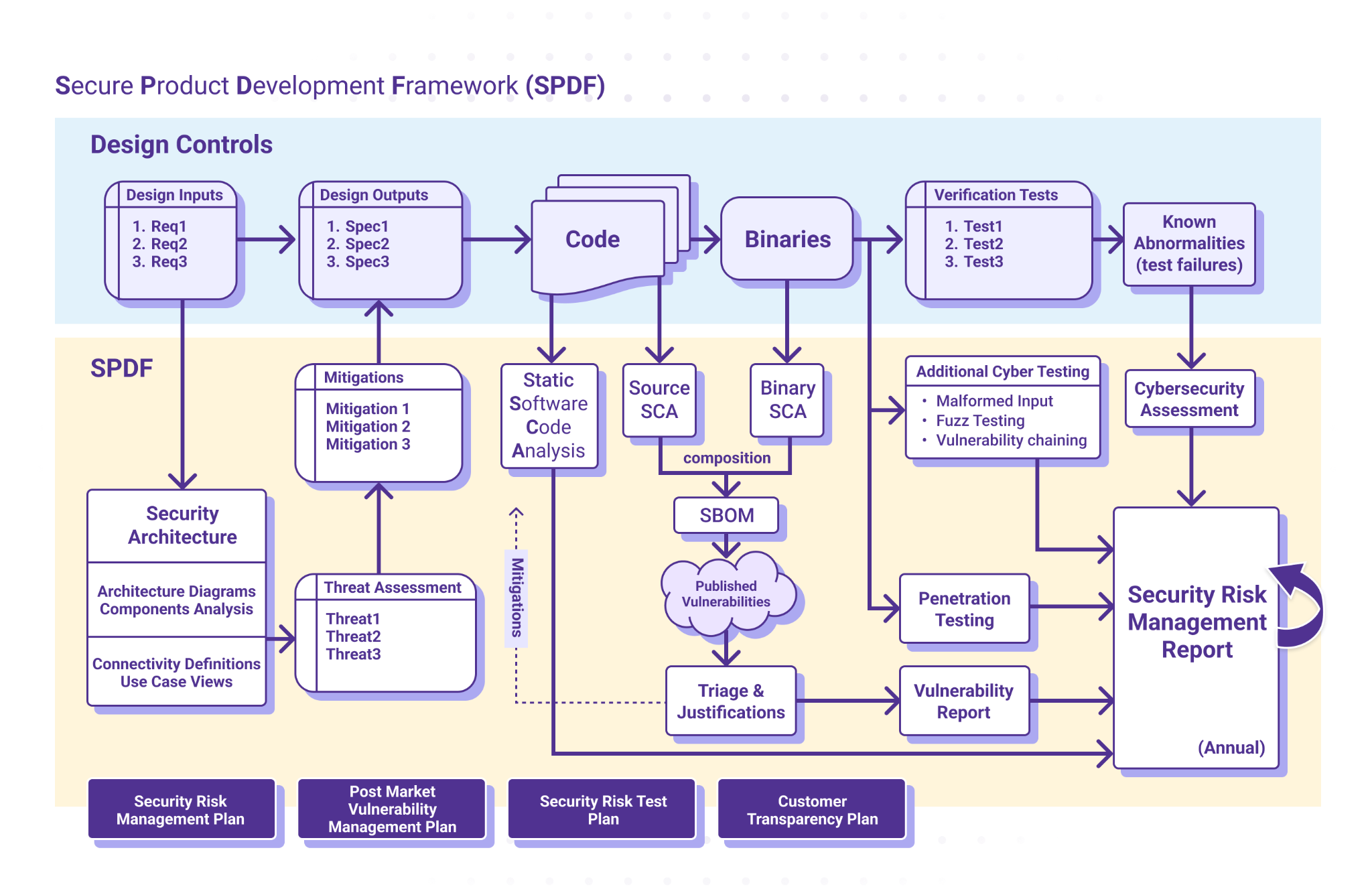
2. Start Early and Integrate SBOM Into Your Product Development Lifecycle
Begin SBOM creation during the early stages of your development lifecycle. Integrate it seamlessly into your existing processes to ensure it becomes a natural part of the workflow. Regularly update the SBOM as software evolves, ensuring that it remains an accurate representation of the device's software components.
3. Include All Software Components
Identify and include all software components, including third-party libraries, open-source software, and proprietary code. Clearly document the version numbers, licenses, and any modifications made to the third-party components. This level of detail is essential for assessing security risks and ensuring compliance. Also document end-of-life (EOL) support, which is significant and required.
4. Standardize Your SBOM Format
Present your SBOM to regulatory authorities, healthcare providers and end-users in a clear and easily understandable, standardized format. This promotes consistency across the industry and facilitates collaboration between stakeholders. It also allows for automation of regularly scheduled vulnerability checking, which can save you significant time and effort.
5. Automate SBOM Vulnerability Checking
Once you’ve generated your SBOM for a given piece of software, use automated tools to check your SBOM against known vulnerabilities contained within national vulnerability databases (NVD). By identifying those components that could pose a threat, you can determine whether you need to remediate any issues.
6. Educate Development Teams
Train development teams on the importance of SBOMs and the role they play in regulatory compliance, and foster a culture of awareness regarding security vulnerabilities and the impact of software composition on the overall device.
7. Conduct Regular Assessments
Conduct regular internal audits to ensure the accuracy and completeness of your SBOM, and submit to external assessments to validate the effectiveness of your SBOM creation and management processes.
8. Stay Informed About Regulatory Changes
Though listed last, this is perhaps the most fundamental and essential best practice: stay abreast of updates to regulatory requirements and industry standards related to SBOMs and adjust your processes accordingly to ensure ongoing compliance and avoid non-compliance penalties.
Need Help Creating Your SBOM?
Creating an SBOM is no longer an optional practice for medical device manufacturers – it's a regulatory necessity. By incorporating these best practices into your development processes, you can not only meet FDA requirements but also enhance the overall security, transparency, and reliability of your medical devices.
But the process can be overwhelming. If you’d like assistance creating an SBOM or would like to compare your existing SBOM against known vulnerabilities, ICS can help. We have a proven track record in medical device development, are well-versed in the intricacies of software composition analysis, regulatory expectations and SBOM best practices, and offer helpful analysis tools to identify software vulnerabilities. Learn more about ICS' cybersecurity solutions or get in touch if you’d like to learn more.
Listen to our on-demand webinar The Real-World Challenges of Medical Device Cybersecurity: Mitigating Vulnerabilities, which includes a discussion of SBOMs.